Specification (Standard Name)
Neue Funktionen
Erste Schritte
- Kurzanleitung für Administrierende
- Kurzanleitung für Benutzende
- Für Entwicklerinnen und Entwickler
- Video-Tutorial-Bibliothek
- Häufig gestellte Fragen
Verwaltung
- Übersicht über die Admin Console
- Benutzendenverwaltung
- Hinzufügen, Bearbeiten und Überprüfen von Benutzenden
- Erstellen von funktionsorientierten Benutzenden
- Überprüfen von Benutzenden, die die Verifizierung nicht abgeschlossen haben
- Suche nach Nutzenden mit Bereitstellungsfehlern
- Ändern des Namens/der E-Mail-Adresse
- Gruppenmitgliedschaft von Benutzenden bearbeiten
- Bearbeiten der Gruppenmitgliedschaft von Benutzenden über die Gruppenoberfläche
- Hochstufen von Benutzenden zu einer Administrationsrolle
- Benutzeridentitätstypen und SSO
- Wechseln der Benutzeridentität
- Authentifizieren von Benutzenden mit MS Azure
- Authentifizieren von Benutzenden mit Google Federation
- Produktprofile
- Anmeldung
- Konto-/Gruppeneinstellungen
- Einstellungsübersicht
- Globale Einstellungen
- Kontoebene und ID
- Neues Empfangserlebnis
- Workflows zum Selbstsignieren
- Massenversand
- Webformulare
- Benutzerdefinierte Sende-Workflows
- Power Automate-Workflows
- Bibliotheksdokumente
- Formulardaten mit Vereinbarungen erfassen
- Eingeschränkte Dokumentsichtbarkeit
- Anhängen einer PDF-Kopie der signierten Vereinbarung
- Einfügen eines Links in eine E-Mail
- Einfügen eines Bilds in eine E-Mail
- An E-Mails angehängte Dateien werden folgendermaßen benannt:
- Anhängen von Audit-Berichten an Dokumente
- Zusammenführen mehrerer Dokumente zu einem Dokument
- Einzelne Dokumente herunterladen
- Signiertes Dokument hochladen
- Delegation für Benutzende in meinem Konto
- Externen Empfangenden das Delegieren erlauben
- Signaturberechtigung
- Sendeberechtigung
- Berechtigung zum Hinzufügen elektronischer Siegel
- Festlegen einer Standardzeitzone
- Festlegen eines Standarddatumsformats
- Benutzende in mehreren Gruppen (UMG)
- Berechtigungen für Gruppenadministrierende
- Empfangende ersetzen
- Audit-Bericht
- Transaktionsfußzeile
- In Produktbotschaften und Anleitungen
- Barrierefreie PDF-Dateien
- Neues Authoring-Erlebnis
- Kundinnen und Kunden im Gesundheitswesen
- Kontoeinrichtung / Branding-Einstellungen
- Signaturvorgaben
- Korrekt formatierte Signaturen
- Empfangenden das Signieren erlauben durch
- Unterzeichnende können ihren Namen ändern
- Empfangenden erlauben, ihre gespeicherte Signatur zu verwenden
- Selbstdefinierte Nutzungsbedingungen und Hinweis für Kundinnen und Kunden
- Empfangende durch Formularfelder leiten
- Vereinbarungs-Workflow neu starten
- Signieren ablehnen
- Stempel-Workflows erlauben
- Unterzeichnende auffordern, ihre Stellenbezeichnung oder ihr Unternehmen anzugeben
- Unterzeichnenden das Drucken und Einfügen von handschriftlichen Signaturen erlauben
- Anzeigen von Nachrichten beim elektronischen Signieren
- Unterzeichnende müssen ein Mobilgerät verwenden, um ihre Signatur zu erstellen
- IP-Adresse von Unterzeichnenden anfordern
- Firmenname und Stellenbezeichnung sollen nicht aus dem Teilnahmestempel ersichtlich sein
- Adaptive Skalierung auf handschriftliche Signatur anwenden
- Digitale Signaturen
- Elektronische Siegel
- Digital Identity
- Berichteinstellungen
- Neues Berichtserlebnis
- Einstellungen für den klassischen Bericht
- Sicherheitseinstellungen
- Einstellungen für Single Sign-on
- Einstellungen zum Merken der Anmeldedaten
- Richtlinien für Anmeldekennwort
- Stärke für Anmeldekennwort
- Dauer der Internet-Sitzung
- Art der PDF-Verschlüsselung
- API
- Zugriff auf Benutzenden- und Gruppeninformationen
- Erlaubte IP-Bereiche
- Kontofreigabe
- Berechtigungen zur Kontofreigabe
- Steuerelemente für das Freigeben von Vereinbarungen
- Bestätigung der Unterzeichnendenidentität
- Kennwort für das Signieren einer Vereinbarung
- Dokumentkennwortstärke
- Unterzeichnende anhand des geografischen Standorts sperren
- Telefonauthentifizierung
- Wissensbasierte Authentifizierung (KBA)
- Zulassen der Seitenextraktion
- Ablauf des Dokumentlinks
- Hochladen eines Clientzertifikats für Webhooks/Rückrufe
- Zeitstempel
- Sendeeinstellungen
- Anzeigen der Seite „Senden“ nach der Anmeldung
- Erfahrungen bei der Erstellung von Vereinbarungen
- Name der Empfangspartei beim Senden erforderlich
- Sperren der Namenswerte für bekannte Benutzende
- Zulässige Empfangsrollen
- E-Witnesses zulassen
- Gruppen empfangender Personen
- CC-Parteien
- Erforderliche Felder
- Anhängen von Dokumenten
- Feldreduzierung
- Vereinbarungen bearbeiten
- Empfangenden aus laufenden Vereinbarungen entfernen
- Eine Kopie (einer Vereinbarung) erstellen
- Vereinbarungsname
- Sprachen
- Private Nachrichten
- Erlaubte Signaturarten
- Erinnerungen
- Kennwortschutz für signierte Dokumente
- Vereinbarungsbenachrichtigung absenden
- Identifikationsoptionen für Unterzeichnende
- Überblick
- Signierkennwort
- Wissensbasierte Authentifizierung
- Telefonauthentifizierung
- WhatsApp-Authentifizierung
- Einmalpasswort per E-Mail
- Acrobat Sign-Authentifizierung
- Cloud-basierte digitale Signatur
- Authentifizierung der digitalen Identität
- Amtl. Lichtbildausweis
- Identitätsberichte der Unterzeichnenden
- Formularfelder mit identitätsverifizierten Daten ausfüllen
- Inhaltsschutz
- Aktivieren von Beglaubigungs-Transaktionen
- Dokumentablauf
- Anzeigen der Vorschau, Positionieren von Signaturen und Hinzufügen von Formularfeldern
- Signierreihenfolge
- Mich hinzufügen
- Link „Vereinbarung herunterladen“
- Formularfeld-Rahmen
- Liquid Mode
- Optionen für selbstdefinierte Workflows
- Upload-Optionen auf der E-Sign-Seite
- Bestätigungs-URL-Umleitung nach der Signatur
- Zugriff auf freigegebene Vereinbarungen einschränken
- Anzeigen der Seite „Senden“ nach der Anmeldung
- Nachrichtenvorlagen
- Bio-Pharma-Einstellungen
- Workflow-Integration
- Beglaubigungs-Einstellungen
- Zahlungsintegration
- Nachrichten für Unterzeichnende
- SAML-Einstellungen
- SAML-Konfiguration
- Installieren des Active Directory Federation Service
- Installieren von Okta
- Installieren von OneLogin
- Installieren von Oracle Identity Federation
- SAML-Konfiguration
- Datennutzungsrechte
- Zeitstempel-Einstellungen
- Externes Archiv
- Kontosprachen
- E-Mail-Einstellungen
- Migration von echosign.com zu adobesign.com
- Konfigurieren von Optionen für Empfangende
- Leitfaden für regulatorische Anforderungen
- Barrierefreiheit
- HIPAA
- DSGVO
- 21 CFR Part 11 und EudraLex Annex 11
- Kundinnen und Kunden im Gesundheitswesen
- IVES-Unterstützung
- Archivieren von Vereinbarungen
- Überlegungen zur EU/dem Vereinigten Königreich
- Gleichzeitiges Herunterladen von mehreren Vereinbarungen
- Anfordern deiner Domäne
- Links „Missbrauch melden“
- Systemanforderungen und Einschränkungen
Senden, Signieren und Verwalten von Vereinbarungen
- Empfangsoptionen
- Stornieren von E-Mail-Erinnerungen
- Optionen auf der E-Signatur-Seite
- Überblick über die E-Signatur-Seite
- Öffnen der Vereinbarung, um sie ohne Felder zu lesen
- Signieren einer Vereinbarung ablehnen
- Delegieren der Signaturberechtigung
- Neustarten der Vereinbarung
- Herunterladen einer PDF-Datei der Vereinbarung
- Anzeigen des Vereinbarungsverlaufs
- Anzeigen der Vereinbarungsnachrichten
- Umwandlung von elektronischer zu handschriftlicher Signatur
- Umwandlung von handschriftlicher zu elektronischer Signatur
- Navigation der Formularfelder
- Löschen der Daten aus den Formularfeldern
- Seitenvergrößerung und Navigation der E-Signatur-Seite
- Ändern der in den Vereinbarungswerkzeugen und -informationen verwendeten Sprache
- Rechtliche Hinweise lesen
- Anpassen der Acrobat Sign-Cookie-Voreinstellungen
- Senden von Vereinbarungen
- Senden (Erstellen) – Seite
- Übersicht über Orientierungspunkte und Funktionen
- Gruppenauswahl
- Hinzufügen von Dateien und Vorlagen
- Vereinbarungsname
- Globale Nachricht
- Ausfülltermin
- Erinnerungen
- Schützen einer PDF-Datei mit Kennwort
- Signaturtyp
- Gebietsschema für die Empfangenden
- Signaturreihenfolge/-fluss der Empfangenden
- Empfängerrollen
- Empfängerauthentifizierung
- Private Nachricht für Empfangende
- Vereinbarungszugriff der Empfangenden
- E-Mail-Adressen der auf CC gesetzten Personen
- Identitätsprüfung
- Senden einer Vereinbarung nur an sich selbst
- Senden einer Vereinbarung an andere
- Handschriftliche Signaturen
- Signierreihenfolge der Empfangenden
- Massenversand
- Senden (Erstellen) – Seite
- Erstellen von Feldern in Dokumenten
- In-App-Authoring-Umgebung
- Automatische Felderkennung
- Ziehen und Ablegen von Feldern in der Authoring-Umgebung
- Formularfelder zu Empfangenden zuweisen
- Die Rolle „Vorausfüllen“
- Anwenden von Feldern mit einer wiederverwendbaren Feldvorlage
- Felder in eine neue Bibliotheksvorlage übertragen
- Aktualisierte Authoring-Umgebung beim Senden von Vereinbarungen
- Erstellen von Formularen mit Text-Tags
- Erstellen von Formularen mit Acrobat (AcroForms)
- Felder
- Feldtypen
- Häufige Feldtypen
- Felder für E-Signaturen
- Initialenfeld
- Namensfeld für empfangende Partei
- E-Mail-Feld für empfangende Partei
- Feld „Signierdatum“
- Textfeld
- Datumsfeld
- Zahlenfeld
- Kontrollkästchen
- Kontrollkästchen
- Optionsfeld
- Dropdown-Menü
- Link-Überlagerung
- Zahlungsfeld
- Anlagen
- Teilnahmestempel
- Transaktionsnummer
- Bild
- Firma
- Titel
- Stempel
- Erscheinungsbild des Feldinhalts
- Feldüberprüfungen
- Werte für maskierte Felder
- Festlegen von Bedingungen für das Ein-/Ausblenden
- Berechnete Felder
- Feldtypen
- Authoring-FAQ
- In-App-Authoring-Umgebung
- Signieren von Vereinbarungen
- Vereinbarungen verwalten
- Übersicht über die Seite „Verwalten“
- Vereinbarung kopieren
- Delegieren von Vereinbarungen
- Ersetzen von Empfangenden
- Eingeschränkte Dokumentsichtbarkeit
- Abbrechen einer Vereinbarung
- Erstellen von neuen Erinnerungen
- Überprüfen von Erinnerungen
- Stornieren von Erinnerungen
- Zugriff auf Power Automate-Flows
- Weitere Aktionen...
- Funktionsweise der Suche
- Anzeigen einer Vereinbarung
- Vorlage aus einer Vereinbarung erstellen
- Aus-/Einblenden von Vereinbarungen
- Hochladen einer signierten Vereinbarung
- Ändern von Dateien und Feldern einer gesendeten Vereinbarung
- Bearbeiten der Authentifizierungsmethode einer Empfangspartei
- Hinzufügen oder Ändern eines Ablaufdatums
- Hinzufügen einer Notiz zu einer Vereinbarung
- Freigabe einer einzelnen Vereinbarung
- Aufheben der Freigabe einer Vereinbarung
- Herunterladen einer einzelnen Vereinbarung
- Herunterladen einzelner Dateien einer Vereinbarung
- Herunterladen des Audit-Berichts einer Vereinbarung
- Herunterladen des Feldinhalts einer Vereinbarung
- Audit-Bericht
- Berichte und Datenexporte
- Überblick
- Zugriffserteilung auf Berichte für Benutzende
- Berichtsdiagramme
- Datenexporte
- Umbenennen eines Berichts/Exports
- Duplizieren eines Berichts/Exports
- Planen eines Berichts/Exports
- Löschen eines Berichts/Exports
- Überprüfen des Transaktionsverbrauchs
Erweiterte Vereinbarungsfunktionen und Workflows
- Webformulare
- Erstellen eines Webformulars
- Bearbeiten eines Webformulars
- Deaktivieren/Aktivieren eines Webformulars
- Ein-/Ausblenden eines Webformulars
- Abrufen der URL oder des Skriptcodes
- Vorausfüllen von Webformularfeldern mithilfe von URL-Parametern
- Speichern eines Webformulars, um es später auszufüllen
- Ändern der Größe eines Webformulars
- Wiederverwendbare Vorlagen (Bibliotheksvorlagen)
- US-Behördenformulare in der Acrobat Sign-Bibliothek
- Erstellen einer Bibliotheksvorlage
- Ändern des Namens einer Bibliotheksvorlage
- Ändern des Typs einer Bibliotheksvorlage
- Ändern der Berechtigungsebene einer Bibliotheksvorlage
- Kopieren, Bearbeiten und Speichern einer freigegebenen Vorlage
- Herunterladen der aggregierten Felddaten für eine Bibliotheksvorlage
- Übertragen des Eigentums an Webformularen und Bibliotheksvorlagen
- Power Automate-Workflows
- Überblick über die Power Automate-Integration und die enthaltenen Berechtigungen
- Aktivieren der Power Automate-Integration
- Kontextbasierte Aktionen auf der Seite „Verwalten“
- Verfolgen der Nutzung von Power Automate
- Erstellen eines neuen Flows (Beispiele)
- Auslöser für Flows
- Importieren von Flows von außerhalb von Acrobat Sign
- Verwalten von Flows
- Bearbeiten von Flows
- Freigeben von Flows
- Deaktivieren oder Aktivieren von Flows
- Löschen von Flows
- Nützliche Vorlagen
- Nur Administration
- Archivierung von Vereinbarungen
- Archivierung von Webformularvereinbarungen
- Speichern abgeschlossener Webformulardokumente in der SharePoint-Bibliothek
- Speichern abgeschlossener Dokumente in OneDrive for Business
- Speichern abgeschlossener Dokumente in Google Drive
- Speichern abgeschlossener Webformulardokumente in Box
- Extrahieren von Vereinbarungsdaten
- Vereinbarungsbenachrichtigungen
- Senden selbstdefinierter E-Mail-Benachrichtigungen mit dem Vereinbarungsinhalt und der signierten Vereinbarung
- Abrufen von Adobe Acrobat Sign-Benachrichtigungen in einem Teams-Kanal
- Abrufen von Adobe Acrobat Sign-Benachrichtigungen in Slack
- Abrufen von Adobe Acrobat Sign-Benachrichtigungen in Webex
- Vereinbarungsgenerierung
- Erstellen eines Dokuments aus einem Power Apps-Formular und einer Word-Vorlage sowie Senden zum Signieren
- Generieren einer Vereinbarung aus einer Word-Vorlage in OneDrive und Einholen der Signatur
- Generieren einer Vereinbarung für ausgewählte Excel-Zeile und Senden zur Überprüfung und Signatur
- Selbstdefinierte Sende-Workflows
- Freigeben von Benutzenden und Vereinbarungen
Integration in andere Produkte
- Übersicht über Acrobat Sign-Integrationen
- Acrobat Sign für Salesforce
- Acrobat Sign für Microsoft
- Weitere Integrationen
- Von Partnern verwaltete Integrationen
- Erstellen eines Integrationsschlüssels
Acrobat Sign-Entwickler
- REST-APIs
- Webhooks
- Sandbox
Support und Fehlerbehebung
Adobe Acrobat Sign includes SAML authentication for customers that desire a federated log in system.
The below document pertains to customer accounts that manage their user licensing directly within the Acrobat Sign application.
Customers that manage user entitlement in the Adobe Admin Console must follow a different process found here.
Introduction
The identity federation standard Security Assertion Markup Language (SAML) 2.0 enables the secure exchange of user authentication data between web applications and identity service providers.
When you use the SAML 2.0 protocol to enable single sign-on (SSO), security tokens containing assertions pass information about an end user (principal) between a SAML authority - an identity
provider (IdP), and a SAML consumer - a service provider (SP).
Acrobat Sign, acting as the service provider (SP), supports single sign-on through SAML using external identity providers (IdPs) such as Okta, OneLogin, Oracle Federated Identity (OIF), and Microsoft Active Directory Federation Service. Acrobat Sign is compatible with all external IdPs that support SAML 2.0.
More information on integrating with these identity providers (IdPs), can be found in the following guides:
- Enabling SAML Single Sign On for Microsoft Active Directory Federation Service
- Enabling SAML Single Sign On for Okta
- Enabling SAML Single Sign On for OneLogin
- Enabling SAML Single Sign-on with Oracle Identity Federation
You can also configure Acrobat Sign for single sign-on (SSO) with other systems already used in your organization, for example, Salesforce.com, or other providers that support SAML 2.0.
Acrobat Sign uses federated authentication as opposed to delegated authentication. Federated authentication does not validate the user's actual password in Acrobat Sign. Instead, Acrobat Sign receives a SAML assertion in an HTTP POST request. Acrobat Sign also supports encrypted assertions.
The SAML assertion has a limited validity period, contains a unique identifier, and is digitally signed. If the assertion is still within its validity period, has an identifier that has not been used before, and has a valid signature from a trusted identity provider, the user is granted access to Acrobat Sign.
A summary of the Acrobat Sign authentication specification is included in the table below:
|
|
Value |
|
Federation Protocol |
SAML 2.0 |
|
Federation Profile |
Browser Post |
|
Federation Unique Identifier |
Email Address |
|
Relay State |
Not Needed. Acrobat Sign has the logic to know where to point the User after they are authenticated. |


Prerequisites
To enable SSO, your corporate network must support the SAML 2.0 protocol. If your corporate network does not support SAML, contact Adobe Acrobat Sign Support to discuss other options to enable Single Sign On in your account.
Before beginning to set up SAML SSO, you must do the following:
- Claim and establish your Domain Name (For the examples in this guide, this will be rrassoc.com.)
- Claiming your Domain is a multi-step process that you should start right away
- Enable SAML for your domain using a provider such as Microsoft Active Directory Federation, Okta, Onelogin, Oracle Identity Federation, or others. You may need to open an Acrobat Sign support ticket to get your domain enabled from the backend
- Create or verify that you have an administrator account with your IdP using an email address
- If you do not have an Okta account, you can create a free Okta Developer Edition organization using this link: https://www.okta.com/developer/signup/
- If you do not have a OneLogin account, you can create a free trials account using this link: https://www.onelogin.com/ and clicking the FREE TRIAL button in the upper right corner
- (Optional) Add an additional email id for User Provisioning in both IdP and SP. This will allow you to add more users who can log in to Acrobat Sign with their SSO credentials
- (Required) Verify that you have an admin user for Acrobat Sign and an Admin user for the IdP
(Optional) Create or verify that you have an Acrobat Sign administrator account that uses the same email address as the account for your IdP (For the examples in this guide, this email address will be susan@rrassoc.com.) This will make it easier for you to administer the accounts - In Acrobat Sign, set your SAML Mode to “SAML Allowed” (See Working with the SAML Settings
for more information.)
When setting up SAML SSO, we recommend that you set the SAML Mode to SAML Allowed until the entire setup process is complete and you’ve verified it is working correctly. Once verified, you can change the SAML Mode to SAML Mandatory.
Enabling Single Sign On using SAML
At a high level, enabling SAML SSO between Acrobat Sign (the SP) and your IdP involves the following high-level steps:
1. If required (by your IdP), set up your IdP using the Acrobat Sign Service Provider (SP) Information
2. Set up Acrobat Sign using information from your IdP
3. Verify that the SAML SSO has been properly set up
Working with SAML Settings
Navigate to Account > Account Settings > SAML Settings


To view the options for User Creation, Login Page Customization, Identity Provider (IdP) Configuration, and Acrobat Sign Service Provider (SP) Information, scroll to the bottom of the SAML Settings page.
SAML Mode Settings
In Acrobat Sign, there are three SAML Mode options and one additional option that works with the SAML Mandatory option.


- SAML Disabled—Disables SAML authentication for the account. When selected, the rest of the SAML configuration page becomes inaccessible.
- SAML Allowed— This option allows users to authenticate to Acrobat Sign by both SAML and the native Acrobat Sign authentication
- SAML Mandatory—Requires that all users authenticate to Acrobat Sign with SAML SSO
- Allow Acrobat Sign Account Administrators to log in using their Acrobat Sign Credentials - When SAML Mandatory is enabled, this option allows Acrobat Sign administrators to be an exception to the SAML rule and authenticate with Acrobat Sign native authentication.
- Admins authenticated using their Acrobat Sign credentials will need to log out twice to log out of the service through the UI controls. (After a successful logout, the admin is taken to their IdP, and because they are logged in to the IdP, the admin gets redirected back to Acrobat Sign and is logged in.)
- Admins authenticated using their Acrobat Sign credentials will need to log out twice to log out of the service through the UI controls. (After a successful logout, the admin is taken to their IdP, and because they are logged in to the IdP, the admin gets redirected back to Acrobat Sign and is logged in.)
- Allow Acrobat Sign Account Administrators to log in using their Acrobat Sign Credentials - When SAML Mandatory is enabled, this option allows Acrobat Sign administrators to be an exception to the SAML rule and authenticate with Acrobat Sign native authentication.
It is strongly recommended that you set the SAML Mode to SAML Allowed until you’ve verified your SAML SSO is working as expected.
Hostname
The Hostname is your domain name. (See Prerequisites above.) When entered, your hostname
becomes part of the Assertion Consumer URL, the Single Log Out (SLO) URL, and Single
Sign-On (Login) URL.


User Creation Settings
Only the first of the two User Creation settings is directly connected with SAML Setup. The second setting pertains to all pending users, whether or not they are added as a result of authenticating through SAML.


- Automatically add users authenticated through SAML—If this option is enabled, users who are authenticated through your IdP are automatically added as pending users in Acrobat Sign
- Automatically make pending users in my account active—If the Require signers in my account to log in to Acrobat Sign before signing setting (Security Settings > Signer Identity Verification), is enabled, this setting should also be enabled. When a signature is requested from a new user, this user is created as a pending user in your account. If this option is not enabled, these users are prevented from signing agreements sent to them for signature
- Allow users who authenticate with SAML to change their email address in their profile - Enable this option to allow your users to change the email address on their Acrobat Sign profile
Login Page Customization Settings
You can customize the sign-on message that users see on the Acrobat Sign Sign In page when SAML Single Sign On is enabled.


- Single Sign On Login Message— Enter a message to display above the SSO Sign In button on the Acrobat Sign Sign In page
- Place the SAML login button at the top of the page when other login options are available - When enabled, the SSO login button will be placed above any other authentication method enabled


Identity Provider (IdP) Configuration Within Acrobat Sign
To set up most IdPs, except as noted for Okta, you must enter information from your IdP into the IdP configuration fields in Acrobat Sign.


- Entity ID/Issuer URL—This value is provided by the IdP to uniquely identify your domain.
- Login URL/SSO Endpoint—The URL that Acrobat Sign will call to request a user login from the IdP. The IdP is responsible for authenticating and logging the user in.
- Logout URL/SLO Endpoint—When someone logs out of Acrobat Sign, this URL is called to log them out of the IdP as well.
- IdP Certificate—The authentication certificate issued by your IdP.
Acrobat Sign SAML Service Provider (SP) Information
The SP information section displays the default information for Acrobat Sign. Once you’ve entered and saved your hostname and IdP Configuration information, the information in the SP information section is updated to include your hostname.
(In our example, https://secure.na1.adobesign.com/public/samlConsume
becomes https://caseyjonez.na1.adobesign.com/public/samlConsume.)


The SP Information provided is as follows:
- Entity ID/SAML Audience—A URL that describes the entity that is expected to receive the SAML message. In this case, it is the URL for Acrobat Sign
- SP Certificate—Some providers require a certificate to be used to identify the Service Provider. The link in this view points to the Acrobat Sign Service Provider certificate
- Assertion Consumer URL— This is the callback that the IdP will send to tell Acrobat Sign to log in a user
- Single Log Out (SLO) URL—The URL that users are redirected to when they log out
- Single Sign-On (Login) URL— This is the URL that the IdP will send login requests to
Microsoft Active Directory Federation Services Configuration
Overview
This document describes the process for setting up Single Sign On for Acrobat Sign using Microsoft Active Directory Federation Service. Before proceeding, please review the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML set up process and provides detailed information on the SAML Settings in Acrobat Sign.
- The process of setting up SAML SSO includes the following:
- Installing the Active Directory Domain Service
- Installing the Active Directory Federation Service
- Creating a Test User
- Adding Acrobat Sign as a relying party
Installing the Active Directory Domain Service
Before configuring SAML for MSAD, you must install the Active Directory Domain Service if it is not already installed. You must have system administrator privileges in Windows Server to install Active Directory Domain Services.
Installing the Active Directory Federation Service
1. If required, launch the Server Manager, then click Dashboard.


2. In the Dashboard, click Add roles and features. The Add Roles and Features Wizard displays.
3. In the Select installation type dialog, select Rule-based or Feature-based Installation then click
Next.


4. In the Select destination server dialog of the wizard, leave the Select a server from the server pool option enabled, select a Server Pool, then click Next.


5. In the Select server roles dialog, select Active Directory Federation Services, then click Next.


6. In the Confirm installation selections dialog of the wizard, accept all the defaults by clicking Install.
7. On the post install options, select Create the first federation server in a federation server farm.
8. On the Welcome page, leave the options as is and click Next.


9. In the Connect to Active Directory Domain Services dialog of the wizard, select the Administrator account if not by default, then click Next.


10. In the Specify Service Properties dialog, import the pfx file that you created using the steps defined in the Certificate Creation section, enter a Federation Service Display Name, then click Next.


11. In the Specify Service Account dialog, select Use an existing domain user account or group Managed Service Account. Use Administrator as the service account and provide your administrator password, then click Next.


12. In the Specify Configuration Database dialog, select Create a database on this server using Windows Internal Database, then click Next.


13. In the Review Options dialog, click Next.


14. In the Prerequisite Checks dialog, once the prerequisite check is done, click Configure.


15. In the Results dialog, ignore the warning and click Close.


Adding Acrobat Sign as a relying party
1. From the Apps menu, launch AD Federation Service Management.


2. In the AD FS console, select Authentication Policies then Edit.


3. In the Edit Global Authentication Policy dialog, under both Extranet and Intranet, enable Forms Authentication.


4. In the AD FS console, under Trust Relationships, select Relying Party Trusts and click Add Relying Party Trust. The Add Relying Party Trust wizard displays.
5. In the Select Data Source dialog of the wizard, enable the Enter Data about the relying party manually option, then click Next.


6. In the Specify Display Name dialog, enter a Display Name, then click Next.


7. In the Choose Profile dialog, enable the AD FS profile option, then click Next.


8. In the Configure Certification dialog there is no certificate to configure, so click Next.


9. In the Configure URL dialog, select Enable support for the SAML 2.0 WebSSO protocol and enter the Assertion Consumer URL from Acrobat Sign, then click Next.
(See the Hostname section of the Single Sign On with SAML Guide for more information about the Assertion Consume URL.)


10. In the Configure Identifiers dialog, enter http://echosign.com for Relying party trust Identifier and click Add, then click Next.


11. In the next screen, leave the defaults as-is, and click Next.


12. In the Choose Issuance Authorization Rules dialog, confirm that the Permit all users to access the relying party option is enabled.


13. In the Ready to Add Trust dialog, click Next.


14. In the Finish dialog, click Close.


15. In the Edit Claim Rules dialog, click Add Rule.


The Add Transform Claim Rule Wizard displays.
16. In the Select Rule Template dialog of the wizard, select Send LDAP Attributes as Claims from the Claim rule template drop-down.


17. In the Configure Rule dialog, select the options shown in the dialog and click Finish. Acrobat Sign only supports the email address as the unique identifier. You need to select E-Mail Addresses as the LDAP Attribute and E-Mail Address as the Outgoing Claim.


18. When the Select Rule Template dialog of the wizard redisplays, select Send Claims Using a Custom Rule from the Claim rule template drop-down, then click Next.


19. In the Configure Rule dialog, enter the following:
- Name of rule—Enter EmailToNameId
- Custom rule description—enter the following:
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type =
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value,
ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"]
= "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress",
Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/spnamequalifier"]
= "");


20. Click Finish. The Add Transform Claim Rule Wizard closes.
21. Back in the Edit Claim Rules for Acrobat Sign dialog, click the Issuance Authorization Rules tab and Delegation Authorization rules tab and ensure that the Permit Access to All Users is enabled for both as shown below.
If not, add a rule, so that Permit Access To All Users is enabled.




22. Click OK to accept all changes can close the Edit Claims Rules for Acrobat Sign dialog.
Adding the Certificate from Acrobat Sign
1. In the AD FS console, under Trust Relationships, select the Acrobat Sign Relying Party click Properties.
2. Once launched, select Authentication Policies and then Edit.


3. Select the Signature tab.
4. Click Add and add the SP certificate file you downloaded from Acrobat Sign.
(See the Adobe Acrobat Sign SAML Service Provider (SP) Information section of the Single Sign On with SAML Guide for more information about the SP certificate.)
5. Select the Advanced tab and change the Secure Hash Algorithm to SHA-2.
6. Select the Endpoints tab and add the Single Logout (SLO) URL from Acrobat Sign.
(See the Hostname section of the Single Sign On with SAML Guide for more information about the Single Logout (SLO) URL).
7. Disable Claims Encryption – Open power shell on the ADFS server and type
8. Set-ADFSRelyingPartyTrust -TargetName "Adobe Sign" -EncryptClaims $false
Acrobat Sign specific settings
- The account should have SAML_AVAILABLE=true
- Host Name
- SAML Mode
- ACCOUNT_USER_ADD_EMAIL_DOMAINS setting to be for example dev.com
- Select the token signing certificate in ADFS and export it as a cer file ( do not export private key) and add it to the account admins SAML Settings page in Acrobat Sign.




Open this certificate file in notepad, and Acrobat Sign Admin copy its contents into the IdP Certificate field in SAML Settings.
Now you should be able to test.
Certificate Creation
1. On Windows, install openssl. On Mac , openssl is present.
2. Launch a command prompt and type:
openssl req -x509 -newkey rsa:2048 -keyout .pem -out .pem -days <#ofdays>
Enter the following:
- Country code- US
- State - Californiacity – San Jose
- Enter some Organization and Organization unit
- Common Name- This is the fully qualified name that is the same as your host system name example sjtest.es.com
3. Now create the pkcs12 key
pkcs12 -export -in <yourkeynameCer> .pem -inkey <yourkeyName> .pem -out my_pkcs12.pfx
4. Enter password when prompted
5. Click Import and select the my_pkcs12.pfx selected above and enter password that you provided at pkcs12 export time when prompted
Okta Configuration
Overview
Acrobat Sign can support Security Assertion Markup Language (SAML) single sign-on (SSO) using external identity providers (IdPs) such as Okta. This document describes the steps for configuring Acrobat Sign for SAML SSO with Okta. This document also provides information on testing your SAML SSO configuration. Before proceeding, please see the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML setup process and provides detailed information on the SAML Settings in Acrobat Sign.
Successful installation requires that your Active Directory have the GivenName (FirstName) and SN (LastName) values populated.
If these values are empty, an Unknown User error will trigger.
Configuring SAML SSO with Okta
You must be an administrator for both your Acrobat Sign and Okta accounts to enable SAML SSO. The username for both accounts must be the same. The passwords can be different.
When enabling SAML SSO with Okta, information only needs to be entered in Acrobat Sign. Okta has developed a custom Acrobat Sign Provisioning app that makes it unnecessary to transfer the SP Information from Acrobat Sign to Okta.
Note: For the most up-to-date instructions for Okta, see http://developer.okta.com/docs/guides/setting_up_a_saml_application_in_okta.html.
1. Log in to Okta and Acrobat Sign in different browsers or in different windows within the same browser.
- In Okta, log in to your account with the same administrator account you use for your Acrobat Sign Admin Account.


- In Acrobat Sign, log in to your account using the same admin account credentials that you use for Okta.


2. Click the blue Admin button.


3. Click the Add Applications shortcut.


The Add Application page displays.


4. In Search, type Acrobat Sign.
- Click the Add button to add the Acrobat Sign Provisioning application.


The Add Acrobat Sign Provisioning wizard launches displaying the General Setting tab.


5. Log in to Acrobat Sign to obtain your Hostname and Acrobat Sign server environment:
- Log in an Acrobat Sign Account Admin
- Navigate to: Account > Account Settings > SAML Settings
- Scroll to the bottom of the page and find the Assertion Consumer URL
- Copy the string between https:// and .adobesign.com/
- The first value is your Hostname
- After the Hostname is the Acrobat Sign environment your account resides on (na1, na2, eu1, jp1, etc.)
- In the below example you would copy rrassoc.na1 (include the dot between values)


6. In Okta under General Settings, enter the Hostname.Instance for your Acrobat Sign account in the Your Acrobat Sign Sub domain field.
Click Next to continue.
Note: If you don’t want users to automatically log in to Acrobat Sign when they log in to Okta, disable the Automatically log in when user lands on the login page option.


7. On the Sign-On Options tab, enable SAML 2.0.


The SAML 2.0 section displays.
8. Under SAML 2.0, click View Setup Instructions.




9. Copy the Entity ID/Issuer URL from the Okta page, and enter it into the Entity ID/Issuer URL field in Acrobat Sign.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)
Note: The "Entity ID/Issuer URL" does not need to be a well formatted URL. It can be an any unique value.


10. Copy the Login URL/SSO Endpoint from the Okta page, and enter it into the Login URL/SSO Endpoint field in Acrobat Sign.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)
Note that in Acrobat Sign, the Logout URL/SLO Endpoint is before the Login URL/SSO Endpoint.


11. Copy the Logout URL/SLO Endpoint from the Okta page and enter it into the Logout URL/SLO Endpoint field in Acrobat Sign.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)


Note: The Logout URL/SLO Endpoint shown above is only a suggestion. You can actually specify any valid URL (e.g., Google).
12. Copy the IdP Certificate from the Okta page to the IdP Certificate field in Acrobat Sign.
- Make sure there are no spaces or returns after “-----END CERTIFICATE-----“.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)


You can close the browser window that displays the Okta How to Configure SAML 2.0 for Acrobat Sign page after you copy the IdP Certificate.
13. In Acrobat Sign, click Save.
14. Click the browser window that displays the Okta Sign-On Options if needed.
15. In the Credential Details section of Sign-On Options (see step 8 above), select Email from the Application username format drop-down, then click Next to continue.


16. Under Provisioning, you have the option to select the Enable provisioning features option. (See Setting up Auto-Provisioning for more information.) Click Next to continue without setting up Auto-provisioning.


Note: If you enable the Enable provisioning features option, you must enable the Automatically add users authenticated through SAML in SAML settings in Acrobat Sign.
17. Under the Assign to People tab, in the People section check the box next to your name to assign at least one active user (yourself), then click Next.


18. Click Done.


You can now log out of Okta and proceed with testing your SAML setup. (See Testing Your Okta SAML SSO Configuration for more information.)
Setting Up Auto-provisioning in Okta
If this option is enabled, and the “Automatically add users authenticated through SAML” option in Acrobat Sign is also enabled, you can automatically provision users in Acrobat Sign.


Setting up Auto-launch for Acrobat Sign
You can automatically launch Acrobat Sign when you log in to Okta. If this feature is enabled, Acrobat Sign will open in a separate window when you log in to Okta. You must have pop-ups enabled in your browser for this feature to work.
Note If you also enabled the “Automatically log in when user lands on login page” option, when you launch Okta two Acrobat Sign windows will open.
1. Log in to Okta. Your Home page will display.
2. On the Acrobat Sign Provisioning app, cursor over the gear icon, then click to activate it.


3. When the Acrobat Sign Provisioning Settings popup displays, click the General tab.


4. Enable the Launch this app when I sign into Okta option.


5. Click Save.
Testing Your Okta SAML SSO Configuration
There are two ways to test your Okta SAML setup.
Log in to Acrobat Sign through Okta
1. If logged in, log out of Okta.
2. Log in to Okta. Your Okta Home page displays.
3. On the Home page, click the Acrobat Sign Provisioning app.


You are automatically logged into Acrobat Sign.


Log in to Acrobat Sign using your URL
1. Enter your company login URL in your browser. The Acrobat Sign Sign In page displays.
2. On the Sign In page, click the second Sign In button. If you’ve entered a custom Single Sign On Login Message that message displays above this button. If you have not entered a custom message, the default message displays.


You are logged into Acrobat Sign.


OneLogin Configuration
Overview
Acrobat Sign can support Security Assertion Markup Language (SAML) single sign-on (SSO) using external identity providers (IdPs) such as OneLogin. This document describes the steps for configuring Acrobat Sign for SAML SSO with OneLogin. This document also provides information on testing your SAML SSO configuration. Before proceeding, please see the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML setup process and provides detailed information on the SAML Settings in Acrobat Sign.
Configuring SAML SSO with OneLogin
1. Log in to OneLogin and Acrobat Sign in different browsers or in different windows within the same browser.
- In OneLogin, log in to your account with the same administrator credentials you use for your Acrobat Sign Admin Account.


- In Acrobat Sign, log in to your account using the same admin account credentials you use for OneLogin. The passwords for these two logins do not have to be the same, but you must log in as the administrator for each account.


2. In OneLogin, click Add Apps.


3. Search for Acrobat Sign.


4. Click the row for Acrobat Sign.


5. In the Add page, under Connectors select SAML 2.0 – user provisioning, then click Save at the top.


6. Navigate to the SAML Settings page. Note the Hostname for Acrobat Sign.


7. In OneLogin, click the Configuration tab. In the Subdomain field, enter your Hostname from Acrobat Sign, then click Save.


8. Click the SSO tab.


9. In the SSO tab, click View Details to display the Standard Strength Certificate (2048-bit) page.


10. In the Standard Strength Certificate page that displays, click the Copy to Clipboard button for the X.509 Certificate field to copy the certificate to the clipboard.


If the certificate successfully copies, the rollover text says “Copy to Clipboard” text updates to “Copied”.
11. In Acrobat Sign, paste the copied certificate into the IdP Certificate field. Be sure to remove any returns that may have been copied. The cursor should be at the end of the last line as shown below.


12. In OneLogin, click the Copy to Clipboard button for the Issuer URL.


13. In Acrobat Sign, paste the Issuer URL into the Entity ID/Issuer URL field.


14. In OneLogin, click the Copy to Clipboard button for the SAML 2.0 Endpoint (HTTP) URL.


15. In Acrobat Sign, right click to paste the SAML 2.0 Endpoint (HTTP) URL in the IdP Login URL field.


16. In OneLogin, click the Copy to Clipboard button next to SLO Endpoint (HTTP).


Note: The OneLogin SAML 2.0 Endpoint URL is only a suggestion. You can actually specify any valid URL (e.g., Google).
17. In Acrobat Sign, copy the SLO Endpoint value into the Logout URL/SLO Endpoint field.


18. In Acrobat Sign, click Save.
19. In OneLogin, click the back arrow to return to the SSO page.


20. Click the Users tab to add users.


21. Click the row to add the user. The Save button is not activated until you click at least one user.


22. When done, click Save.
Testing Your OneLogin SAML SSO Configuration
There are two ways to test your OneLogin SAML Setup.
Log in to Acrobat Sign through OneLogin
1. If logged in, log out of Acrobat Sign.
2. Log in to OneLogin.


3. On the App Home page, click the Acrobat Sign app.


You are automatically logged into Acrobat Sign.


Log in to Acrobat Sign using your URL
1. Enter your company login URL for Acrobat Sign in the address line of your browser (such as myCompany.adobesign.com). The Acrobat Sign Sign In page
displays.
2. On the Sign In page, click the second Sign In button. If you’ve entered a custom Single Sign On Login Message that message displays above this button. If you have not entered a custom message, the default message displays.


3. You are logged into Acrobat Sign.


Oracle Identity Federation Configuration
Overview
Acrobat Sign can support Security Assertion Markup Language (SAML) single sign-on (SSO) using external identity providers (IdPs) such as Oracle Identity Federation (11g). This document describes the steps for configuring Acrobat Sign, acting as the SAML consumer or service provider (SP), to use OIF. This document also provides suggested steps for configuring OIF, however, please contact your OIF system administrator before making any configuration changes to your OIF Server. Before proceeding, please see the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML set up process and provides detailed information on the SAML Settings in Acrobat Sign.
Configuring OIF as an IdP in Acrobat Sign
Your organization’s instance of OIF needs to be configured within Acrobat Sign as the external SAML Identity Provider (IdP). As an administrator for your Acrobat Sign Account, navigate to SAML Setting in Acrobat Sign as an (Account | Account Settings | SAML Settings).
You will need metadata information from your OIF IdP
configuration. Typically, the metadata for the OIF is available as an XML
content at: http://:/fed/idp/metadata.
Please contact your OIF administrator to gather the relevant. You will need the
following configuration information.
- Entity ID/Issuer URL—The entityID attribute on EntityDescriptor element
- Logout URL/SLO Endpoint—When someone logs out of Acrobat Sign, this URL is called to log them out of the IdP as well.
- Login URL/SSO Endpoint—The Location attribute on SingleSignOnService element
- IdP Certificate—Certificate information under the element EntityDescriptor -> IDPSSODescriptor -> KeyDescriptor use="signing"
This information should be configured in the appropriate fields in the Acrobat Sign SAML configuration. See the image below:
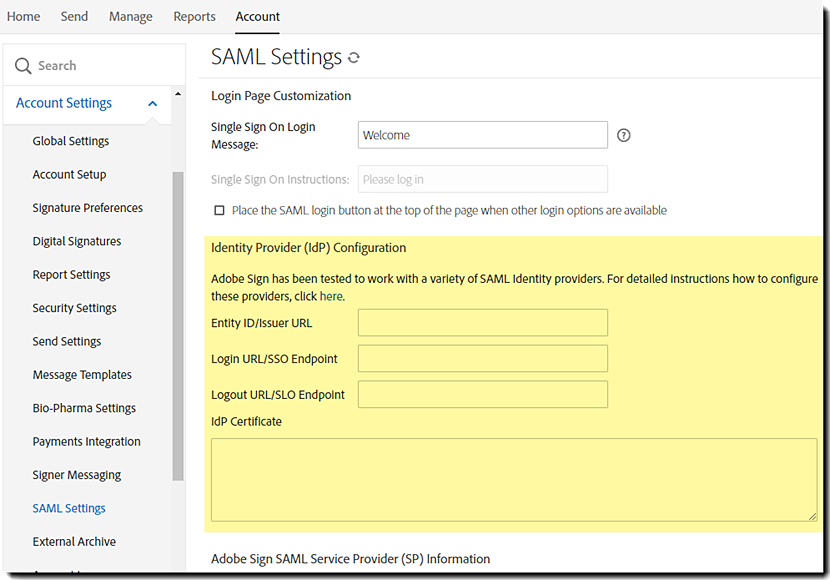

Configuring Acrobat Sign as a SP in OIF
Once the OIF SAML configuration is complete within the Acrobat Sign UI, the next step is to configure Acrobat Sign as a Service Provider within OIF. The information required for configuring Acrobat Sign within OIF is available on the Acrobat Sign SAML Service Provider (SP) information section under Account | Account Settings | SAML Settings.


The metadata description for Acrobat Sign is shown below:


You must customize this metadata description and change the highlighted section in the XML to match the URL for your account. The Assertion Consumer URL for your specific account is shown in SAML Settings.
The steps for completing the configuration in OIF are as follows:
1. Go to the Federations configuration screen on the OIF Administration panel


2. Create a new federation profile


3. Create a new Service Provider (SP) listing for Acrobat Sign.
Import the Acrobat Sign SP configuration XML or manually create the SP listing using the provider information from the Acrobat Sign SAML settings.


4. Complete the configuration. Acrobat Sign will appear as a new Service Provider listing in the OIF list of SPs.


Verifying Email Address as NameID Format
Acrobat Sign uses email addresses as the unique user identifier. Before testing the single sign-on one last step is the ensure that the email address field is mapped to the appropriate user attribute within OIF and that the email address is enabled as a valid NameID format.




Known Issues
Redhat IdP has a setting called Encrypt Assertions that adds an additional layer of encryption.
This additional encryption is incompatible with the Acrobat Sign SAML configuration, and should not be enabled for Acrobat Sign.


©2022 Adobe Systems Incorporated. All Rights Reserved.
Products mentioned in this document, such as the services of identity providers Microsoft Active Directory Federation, Okta, Onelogin, and Oracle Identity Federation, and Salesforce software retain all of the copyrights and trademark rights of their specific corporations.