Specification (Standard Name)
新增功能
快速入门
管理
- Admin Console 概述
- 用户管理
- 添加、编辑和审阅活动用户
- 创建以功能为中心的用户
- 查看尚未完成验证的用户
- 检查是否有用户存在配置错误
- 更改姓名/电子邮件地址
- 编辑用户的组成员资格
- 通过组界面编辑用户的组成员资格
- 将用户提升为管理员角色
- 用户身份类型和 SSO
- 切换用户标识
- 使用 MS Azure 对用户进行身份验证
- 使用 Google 联合身份验证对用户进行身份验证
- 产品配置文件
- 登录体验
- 帐户/组设置
- 设置概述
- 全局设置
- 帐户层级和 ID
- 全新的收件人体验
- 自签名工作流
- 批量发送
- Web 表单
- 自定义发送工作流
- Power Automate 工作流
- 库文档
- 收集包含协议的表单数据
- 有限文件可见性
- 附加已签名协议的 PDF 副本
- 在电子邮件中包含链接
- 在电子邮件中包含图像
- 附加至电子邮件的文件将命名为
- 将审核报告附加到文档
- 将多个文档合并为一个
- 下载单个文档
- 上传签名文档
- 我的帐户中的用户委托
- 允许外部收件人委派
- 授权签名
- 授权发送
- 授权添加电子密封
- 设置默认时区
- 设置默认日期格式
- 位于多个组的用户 (UMG)
- 组管理员权限
- 替换收件人
- 审核报告
- 事务页脚
- 在产品消息发送和指南中
- 可访问的 PDF
- 新版“编辑”体验
- 医疗保健客户
- 帐户设置/品牌设置
- 签名首选项
- 格式精美的签名
- 允许收件人签名的方式
- 签名者可以更改其姓名
- 允许收件人使用其保存的签名
- 自定义使用条款和消费者信息披露条款
- 在表单字段中导航收件人
- 重启协议工作流
- 拒绝签名
- 允许图章工作流
- 要求签名者提供其职务或公司
- 允许签名者打印并置入书面签名
- 进行电子签名时显示消息
- 需要签名者使用移动设备创建其签名
- 请求签名者的 IP 地址
- 从参与者图章中排除公司名称和职务
- 应用自适应签名绘制缩放比例
- 数字签名
- 电子签章
- 数字身份
- 报告设置
- 新版报告体验
- 经典报告设置
- 安全设置
- 发送设置
- 登录后显示“发送”页面
- 协议创建体验
- 发送时需要收件人姓名
- 锁定已知用户的名称值
- 允许的收件人角色
- 允许电子见证人
- 收件人组
- CC
- 必填字段
- 附加文件
- 字段拼合
- 修改协议
- 从进行中的协议中移除收件人
- 创建协议副本
- 协议名称
- 语言
- 私人消息
- 允许的签名类型
- 提醒
- 已签名文档的密码保护
- 通过以下方式发送协议通知
- 签名者身份识别选项
- 使用经身份验证的数据填充表单字段
- 内容保护
- 启用 Notarize 事务
- 文档过期
- 预览、定位签名和添加字段
- 签名顺序
- 添加我自己
- 下载协议链接
- 表单字段边框
- “液体”模式
- 自定义工作流控件
- 电子签名页面的上传选项
- 签名后确认 URL 重定向
- 限制对共享协议的访问权限
- 登录后显示“发送”页面
- 消息模板
- 生物识别设置
- 工作流集成
- 公证设置
- 付款集成
- 签名者消息发送
- SAML 设置
- SAML 配置
- 安装 Microsoft Active Directory 联合身份验证服务
- 安装 Okta
- 安装 OneLogin
- 安装 Oracle Identity Federation
- SAML 配置
- 数据管理
- 时间戳设置
- 外部归档
- 帐户语言
- 电子邮件设置
- 从 echosign.com 迁移到 adobesign.com
- 为收件人配置选项
- 监管要求指导
- 批量下载协议
- 申请您的域
- “举报滥用”链接
- 系统要求和限制
发送、签署和管理协议
- 收件人选项
- 发送协议
- 在文档中创作字段
- 应用程序内创作环境
- 自动字段检测
- 使用创作环境拖放字段
- 向收件人分配表单字段
- 预填充角色
- 使用可重复使用的字段模板应用字段
- 将字段传输到新库模板
- 更新了发送协议时的创作环境
- 使用文本标记创建表单
- 使用 Acrobat (AcroForms) 创建表单
- 字段
- 创作常见问题
- 应用程序内创作环境
- 签署协议
- 管理协议
- 审核报告
- 报告和数据导出文件
高级协议功能和工作流
- Web 表单
- 可重复使用的模板(库模板)
- 转让 Web 表单和库模板的所有权
- Power Automate 工作流
- Power Automate 集成和包含的权限概述
- 启用 Power Automate 集成
- “管理”页面上的上下文操作
- 跟踪 Power Automate 使用情况
- 创建新的工作流(示例)
- 用于工作流的触发器
- 从 Acrobat Sign 外部导入工作流
- 管理工作流
- 编辑工作流
- 共享工作流
- 禁用或启用工作流
- 删除工作流
- 实用模板
- 仅限管理员
- 协议存档
- Web 表单协议存档
- 将已完成的 Web 表单文档保存到 SharePoint 库
- 将已完成的 Web 表单文档保存到 OneDrive for Business
- 将已完成的文档保存到 Google Drive
- 将已完成的 Web 表单文档保存到 Box
- 协议数据提取
- 协议通知
- 发送包含协议内容和已签名协议的自定义电子邮件通知
- 在 Teams 渠道中获取 Adobe Acrobat Sign 通知
- 在 Slack 中获取 Adobe Acrobat Sign 通知
- 在 Webex 中获取 Adobe Acrobat Sign 通知
- 协议生成
- 通过 Power Apps 表单和 Word 模板生成文档,并发送以供签名
- 从 OneDrive 中的 Word 模板生成协议并获取签名
- 为所选 Excel 行生成协议,发送以供审阅和签名
- 自定义发送工作流
- 共享用户和协议
与其他产品集成
- Acrobat Sign 集成概述
- Acrobat Sign for Salesforce
- Acrobat Sign for Microsoft
- 其他集成
- 合作伙伴管理的集成
- 如何获取集成密钥
Acrobat Sign 开发人员
- REST API
- Webhook
- 沙盒
支持和故障排除
Adobe Acrobat Sign includes SAML authentication for customers that desire a federated log in system.
The below document pertains to customer accounts that manage their user licensing directly within the Acrobat Sign application.
Customers that manage user entitlement in the Adobe Admin Console must follow a different process found here.
Introduction
The identity federation standard Security Assertion Markup Language (SAML) 2.0 enables the secure exchange of user authentication data between web applications and identity service providers.
When you use the SAML 2.0 protocol to enable single sign-on (SSO), security tokens containing assertions pass information about an end user (principal) between a SAML authority - an identity
provider (IdP), and a SAML consumer - a service provider (SP).
Acrobat Sign, acting as the service provider (SP), supports single sign-on through SAML using external identity providers (IdPs) such as Okta, OneLogin, Oracle Federated Identity (OIF), and Microsoft Active Directory Federation Service. Acrobat Sign is compatible with all external IdPs that support SAML 2.0.
More information on integrating with these identity providers (IdPs), can be found in the following guides:
- Enabling SAML Single Sign On for Microsoft Active Directory Federation Service
- Enabling SAML Single Sign On for Okta
- Enabling SAML Single Sign On for OneLogin
- Enabling SAML Single Sign-on with Oracle Identity Federation
You can also configure Acrobat Sign for single sign-on (SSO) with other systems already used in your organization, for example, Salesforce.com, or other providers that support SAML 2.0.
Acrobat Sign uses federated authentication as opposed to delegated authentication. Federated authentication does not validate the user's actual password in Acrobat Sign. Instead, Acrobat Sign receives a SAML assertion in an HTTP POST request. Acrobat Sign also supports encrypted assertions.
The SAML assertion has a limited validity period, contains a unique identifier, and is digitally signed. If the assertion is still within its validity period, has an identifier that has not been used before, and has a valid signature from a trusted identity provider, the user is granted access to Acrobat Sign.
A summary of the Acrobat Sign authentication specification is included in the table below:
|
|
Value |
|
Federation Protocol |
SAML 2.0 |
|
Federation Profile |
Browser Post |
|
Federation Unique Identifier |
Email Address |
|
Relay State |
Not Needed. Acrobat Sign has the logic to know where to point the User after they are authenticated. |


Prerequisites
To enable SSO, your corporate network must support the SAML 2.0 protocol. If your corporate network does not support SAML, contact Adobe Acrobat Sign Support to discuss other options to enable Single Sign On in your account.
Before beginning to set up SAML SSO, you must do the following:
- Claim and establish your Domain Name (For the examples in this guide, this will be rrassoc.com.)
- Claiming your Domain is a multi-step process that you should start right away
- Enable SAML for your domain using a provider such as Microsoft Active Directory Federation, Okta, Onelogin, Oracle Identity Federation, or others. You may need to open an Acrobat Sign support ticket to get your domain enabled from the backend
- Create or verify that you have an administrator account with your IdP using an email address
- If you do not have an Okta account, you can create a free Okta Developer Edition organization using this link: https://www.okta.com/developer/signup/
- If you do not have a OneLogin account, you can create a free trials account using this link: https://www.onelogin.com/ and clicking the FREE TRIAL button in the upper right corner
- (Optional) Add an additional email id for User Provisioning in both IdP and SP. This will allow you to add more users who can log in to Acrobat Sign with their SSO credentials
- (Required) Verify that you have an admin user for Acrobat Sign and an Admin user for the IdP
(Optional) Create or verify that you have an Acrobat Sign administrator account that uses the same email address as the account for your IdP (For the examples in this guide, this email address will be susan@rrassoc.com.) This will make it easier for you to administer the accounts - In Acrobat Sign, set your SAML Mode to “SAML Allowed” (See Working with the SAML Settings
for more information.)
When setting up SAML SSO, we recommend that you set the SAML Mode to SAML Allowed until the entire setup process is complete and you’ve verified it is working correctly. Once verified, you can change the SAML Mode to SAML Mandatory.
Enabling Single Sign On using SAML
At a high level, enabling SAML SSO between Acrobat Sign (the SP) and your IdP involves the following high-level steps:
1. If required (by your IdP), set up your IdP using the Acrobat Sign Service Provider (SP) Information
2. Set up Acrobat Sign using information from your IdP
3. Verify that the SAML SSO has been properly set up
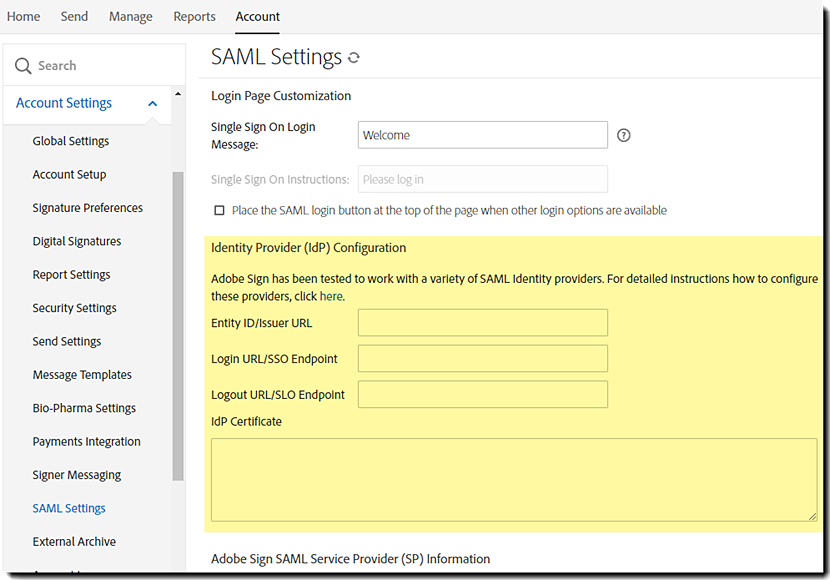
Working with SAML Settings
Navigate to Account > Account Settings > SAML Settings


To view the options for User Creation, Login Page Customization, Identity Provider (IdP) Configuration, and Acrobat Sign Service Provider (SP) Information, scroll to the bottom of the SAML Settings page.
SAML Mode Settings
In Acrobat Sign, there are three SAML Mode options and one additional option that works with the SAML Mandatory option.


- SAML Disabled—Disables SAML authentication for the account. When selected, the rest of the SAML configuration page becomes inaccessible.
- SAML Allowed— This option allows users to authenticate to Acrobat Sign by both SAML and the native Acrobat Sign authentication
- SAML Mandatory—Requires that all users authenticate to Acrobat Sign with SAML SSO
- Allow Acrobat Sign Account Administrators to log in using their Acrobat Sign Credentials - When SAML Mandatory is enabled, this option allows Acrobat Sign administrators to be an exception to the SAML rule and authenticate with Acrobat Sign native authentication.
- Admins authenticated using their Acrobat Sign credentials will need to log out twice to log out of the service through the UI controls. (After a successful logout, the admin is taken to their IdP, and because they are logged in to the IdP, the admin gets redirected back to Acrobat Sign and is logged in.)
- Admins authenticated using their Acrobat Sign credentials will need to log out twice to log out of the service through the UI controls. (After a successful logout, the admin is taken to their IdP, and because they are logged in to the IdP, the admin gets redirected back to Acrobat Sign and is logged in.)
- Allow Acrobat Sign Account Administrators to log in using their Acrobat Sign Credentials - When SAML Mandatory is enabled, this option allows Acrobat Sign administrators to be an exception to the SAML rule and authenticate with Acrobat Sign native authentication.
It is strongly recommended that you set the SAML Mode to SAML Allowed until you’ve verified your SAML SSO is working as expected.
Hostname
The Hostname is your domain name. (See Prerequisites above.) When entered, your hostname
becomes part of the Assertion Consumer URL, the Single Log Out (SLO) URL, and Single
Sign-On (Login) URL.


User Creation Settings
Only the first of the two User Creation settings is directly connected with SAML Setup. The second setting pertains to all pending users, whether or not they are added as a result of authenticating through SAML.


- Automatically add users authenticated through SAML—If this option is enabled, users who are authenticated through your IdP are automatically added as pending users in Acrobat Sign
- Automatically make pending users in my account active—If the Require signers in my account to log in to Acrobat Sign before signing setting (Security Settings > Signer Identity Verification), is enabled, this setting should also be enabled. When a signature is requested from a new user, this user is created as a pending user in your account. If this option is not enabled, these users are prevented from signing agreements sent to them for signature
- Allow users who authenticate with SAML to change their email address in their profile - Enable this option to allow your users to change the email address on their Acrobat Sign profile
Login Page Customization Settings
You can customize the sign-on message that users see on the Acrobat Sign Sign In page when SAML Single Sign On is enabled.


- Single Sign On Login Message— Enter a message to display above the SSO Sign In button on the Acrobat Sign Sign In page
- Place the SAML login button at the top of the page when other login options are available - When enabled, the SSO login button will be placed above any other authentication method enabled


Identity Provider (IdP) Configuration Within Acrobat Sign
To set up most IdPs, except as noted for Okta, you must enter information from your IdP into the IdP configuration fields in Acrobat Sign.


- Entity ID/Issuer URL—This value is provided by the IdP to uniquely identify your domain.
- Login URL/SSO Endpoint—The URL that Acrobat Sign will call to request a user login from the IdP. The IdP is responsible for authenticating and logging the user in.
- Logout URL/SLO Endpoint—When someone logs out of Acrobat Sign, this URL is called to log them out of the IdP as well.
- IdP Certificate—The authentication certificate issued by your IdP.
Acrobat Sign SAML Service Provider (SP) Information
The SP information section displays the default information for Acrobat Sign. Once you’ve entered and saved your hostname and IdP Configuration information, the information in the SP information section is updated to include your hostname.
(In our example, https://secure.na1.adobesign.com/public/samlConsume
becomes https://caseyjonez.na1.adobesign.com/public/samlConsume.)


The SP Information provided is as follows:
- Entity ID/SAML Audience—A URL that describes the entity that is expected to receive the SAML message. In this case, it is the URL for Acrobat Sign
- SP Certificate—Some providers require a certificate to be used to identify the Service Provider. The link in this view points to the Acrobat Sign Service Provider certificate
- Assertion Consumer URL— This is the callback that the IdP will send to tell Acrobat Sign to log in a user
- Single Log Out (SLO) URL—The URL that users are redirected to when they log out
- Single Sign-On (Login) URL— This is the URL that the IdP will send login requests to
Microsoft Active Directory Federation Services Configuration
Overview
This document describes the process for setting up Single Sign On for Acrobat Sign using Microsoft Active Directory Federation Service. Before proceeding, please review the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML set up process and provides detailed information on the SAML Settings in Acrobat Sign.
- The process of setting up SAML SSO includes the following:
- Installing the Active Directory Domain Service
- Installing the Active Directory Federation Service
- Creating a Test User
- Adding Acrobat Sign as a relying party
Installing the Active Directory Domain Service
Before configuring SAML for MSAD, you must install the Active Directory Domain Service if it is not already installed. You must have system administrator privileges in Windows Server to install Active Directory Domain Services.
Installing the Active Directory Federation Service
1. If required, launch the Server Manager, then click Dashboard.


2. In the Dashboard, click Add roles and features. The Add Roles and Features Wizard displays.
3. In the Select installation type dialog, select Rule-based or Feature-based Installation then click
Next.


4. In the Select destination server dialog of the wizard, leave the Select a server from the server pool option enabled, select a Server Pool, then click Next.


5. In the Select server roles dialog, select Active Directory Federation Services, then click Next.


6. In the Confirm installation selections dialog of the wizard, accept all the defaults by clicking Install.
7. On the post install options, select Create the first federation server in a federation server farm.
8. On the Welcome page, leave the options as is and click Next.


9. In the Connect to Active Directory Domain Services dialog of the wizard, select the Administrator account if not by default, then click Next.


10. In the Specify Service Properties dialog, import the pfx file that you created using the steps defined in the Certificate Creation section, enter a Federation Service Display Name, then click Next.


11. In the Specify Service Account dialog, select Use an existing domain user account or group Managed Service Account. Use Administrator as the service account and provide your administrator password, then click Next.


12. In the Specify Configuration Database dialog, select Create a database on this server using Windows Internal Database, then click Next.


13. In the Review Options dialog, click Next.


14. In the Prerequisite Checks dialog, once the prerequisite check is done, click Configure.


15. In the Results dialog, ignore the warning and click Close.


Adding Acrobat Sign as a relying party
1. From the Apps menu, launch AD Federation Service Management.


2. In the AD FS console, select Authentication Policies then Edit.


3. In the Edit Global Authentication Policy dialog, under both Extranet and Intranet, enable Forms Authentication.


4. In the AD FS console, under Trust Relationships, select Relying Party Trusts and click Add Relying Party Trust. The Add Relying Party Trust wizard displays.
5. In the Select Data Source dialog of the wizard, enable the Enter Data about the relying party manually option, then click Next.


6. In the Specify Display Name dialog, enter a Display Name, then click Next.


7. In the Choose Profile dialog, enable the AD FS profile option, then click Next.


8. In the Configure Certification dialog there is no certificate to configure, so click Next.


9. In the Configure URL dialog, select Enable support for the SAML 2.0 WebSSO protocol and enter the Assertion Consumer URL from Acrobat Sign, then click Next.
(See the Hostname section of the Single Sign On with SAML Guide for more information about the Assertion Consume URL.)


10. In the Configure Identifiers dialog, enter http://echosign.com for Relying party trust Identifier and click Add, then click Next.


11. In the next screen, leave the defaults as-is, and click Next.


12. In the Choose Issuance Authorization Rules dialog, confirm that the Permit all users to access the relying party option is enabled.


13. In the Ready to Add Trust dialog, click Next.


14. In the Finish dialog, click Close.


15. In the Edit Claim Rules dialog, click Add Rule.


The Add Transform Claim Rule Wizard displays.
16. In the Select Rule Template dialog of the wizard, select Send LDAP Attributes as Claims from the Claim rule template drop-down.


17. In the Configure Rule dialog, select the options shown in the dialog and click Finish. Acrobat Sign only supports the email address as the unique identifier. You need to select E-Mail Addresses as the LDAP Attribute and E-Mail Address as the Outgoing Claim.


18. When the Select Rule Template dialog of the wizard redisplays, select Send Claims Using a Custom Rule from the Claim rule template drop-down, then click Next.


19. In the Configure Rule dialog, enter the following:
- Name of rule—Enter EmailToNameId
- Custom rule description—enter the following:
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type =
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value,
ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"]
= "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress",
Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/spnamequalifier"]
= "");


20. Click Finish. The Add Transform Claim Rule Wizard closes.
21. Back in the Edit Claim Rules for Acrobat Sign dialog, click the Issuance Authorization Rules tab and Delegation Authorization rules tab and ensure that the Permit Access to All Users is enabled for both as shown below.
If not, add a rule, so that Permit Access To All Users is enabled.




22. Click OK to accept all changes can close the Edit Claims Rules for Acrobat Sign dialog.
Adding the Certificate from Acrobat Sign
1. In the AD FS console, under Trust Relationships, select the Acrobat Sign Relying Party click Properties.
2. Once launched, select Authentication Policies and then Edit.


3. Select the Signature tab.
4. Click Add and add the SP certificate file you downloaded from Acrobat Sign.
(See the Adobe Acrobat Sign SAML Service Provider (SP) Information section of the Single Sign On with SAML Guide for more information about the SP certificate.)
5. Select the Advanced tab and change the Secure Hash Algorithm to SHA-2.
6. Select the Endpoints tab and add the Single Logout (SLO) URL from Acrobat Sign.
(See the Hostname section of the Single Sign On with SAML Guide for more information about the Single Logout (SLO) URL).
7. Disable Claims Encryption – Open power shell on the ADFS server and type
8. Set-ADFSRelyingPartyTrust -TargetName "Adobe Sign" -EncryptClaims $false
Acrobat Sign specific settings
- The account should have SAML_AVAILABLE=true
- Host Name
- SAML Mode
- ACCOUNT_USER_ADD_EMAIL_DOMAINS setting to be for example dev.com
- Select the token signing certificate in ADFS and export it as a cer file ( do not export private key) and add it to the account admins SAML Settings page in Acrobat Sign.




Open this certificate file in notepad, and Acrobat Sign Admin copy its contents into the IdP Certificate field in SAML Settings.
Now you should be able to test.
Certificate Creation
1. On Windows, install openssl. On Mac , openssl is present.
2. Launch a command prompt and type:
openssl req -x509 -newkey rsa:2048 -keyout .pem -out .pem -days <#ofdays>
Enter the following:
- Country code- US
- State - Californiacity – San Jose
- Enter some Organization and Organization unit
- Common Name- This is the fully qualified name that is the same as your host system name example sjtest.es.com
3. Now create the pkcs12 key
pkcs12 -export -in <yourkeynameCer> .pem -inkey <yourkeyName> .pem -out my_pkcs12.pfx
4. Enter password when prompted
5. Click Import and select the my_pkcs12.pfx selected above and enter password that you provided at pkcs12 export time when prompted
Okta Configuration
Overview
Acrobat Sign can support Security Assertion Markup Language (SAML) single sign-on (SSO) using external identity providers (IdPs) such as Okta. This document describes the steps for configuring Acrobat Sign for SAML SSO with Okta. This document also provides information on testing your SAML SSO configuration. Before proceeding, please see the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML setup process and provides detailed information on the SAML Settings in Acrobat Sign.
Successful installation requires that your Active Directory have the GivenName (FirstName) and SN (LastName) values populated.
If these values are empty, an Unknown User error will trigger.
Configuring SAML SSO with Okta
You must be an administrator for both your Acrobat Sign and Okta accounts to enable SAML SSO. The username for both accounts must be the same. The passwords can be different.
When enabling SAML SSO with Okta, information only needs to be entered in Acrobat Sign. Okta has developed a custom Acrobat Sign Provisioning app that makes it unnecessary to transfer the SP Information from Acrobat Sign to Okta.
Note: For the most up-to-date instructions for Okta, see http://developer.okta.com/docs/guides/setting_up_a_saml_application_in_okta.html.
1. Log in to Okta and Acrobat Sign in different browsers or in different windows within the same browser.
- In Okta, log in to your account with the same administrator account you use for your Acrobat Sign Admin Account.


- In Acrobat Sign, log in to your account using the same admin account credentials that you use for Okta.


2. Click the blue Admin button.


3. Click the Add Applications shortcut.


The Add Application page displays.


4. In Search, type Acrobat Sign.
- Click the Add button to add the Acrobat Sign Provisioning application.


The Add Acrobat Sign Provisioning wizard launches displaying the General Setting tab.


5. Log in to Acrobat Sign to obtain your Hostname and Acrobat Sign server environment:
- Log in an Acrobat Sign Account Admin
- Navigate to: Account > Account Settings > SAML Settings
- Scroll to the bottom of the page and find the Assertion Consumer URL
- Copy the string between https:// and .adobesign.com/
- The first value is your Hostname
- After the Hostname is the Acrobat Sign environment your account resides on (na1, na2, eu1, jp1, etc.)
- In the below example you would copy rrassoc.na1 (include the dot between values)


6. In Okta under General Settings, enter the Hostname.Instance for your Acrobat Sign account in the Your Acrobat Sign Sub domain field.
Click Next to continue.
Note: If you don’t want users to automatically log in to Acrobat Sign when they log in to Okta, disable the Automatically log in when user lands on the login page option.


7. On the Sign-On Options tab, enable SAML 2.0.


The SAML 2.0 section displays.
8. Under SAML 2.0, click View Setup Instructions.




9. Copy the Entity ID/Issuer URL from the Okta page, and enter it into the Entity ID/Issuer URL field in Acrobat Sign.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)
Note: The "Entity ID/Issuer URL" does not need to be a well formatted URL. It can be an any unique value.


10. Copy the Login URL/SSO Endpoint from the Okta page, and enter it into the Login URL/SSO Endpoint field in Acrobat Sign.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)
Note that in Acrobat Sign, the Logout URL/SLO Endpoint is before the Login URL/SSO Endpoint.


11. Copy the Logout URL/SLO Endpoint from the Okta page and enter it into the Logout URL/SLO Endpoint field in Acrobat Sign.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)


Note: The Logout URL/SLO Endpoint shown above is only a suggestion. You can actually specify any valid URL (e.g., Google).
12. Copy the IdP Certificate from the Okta page to the IdP Certificate field in Acrobat Sign.
- Make sure there are no spaces or returns after “-----END CERTIFICATE-----“.
(see the idP Configuration section of the How to Configure SAML 2.0 for Acrobat Sign)


You can close the browser window that displays the Okta How to Configure SAML 2.0 for Acrobat Sign page after you copy the IdP Certificate.
13. In Acrobat Sign, click Save.
14. Click the browser window that displays the Okta Sign-On Options if needed.
15. In the Credential Details section of Sign-On Options (see step 8 above), select Email from the Application username format drop-down, then click Next to continue.


16. Under Provisioning, you have the option to select the Enable provisioning features option. (See Setting up Auto-Provisioning for more information.) Click Next to continue without setting up Auto-provisioning.


Note: If you enable the Enable provisioning features option, you must enable the Automatically add users authenticated through SAML in SAML settings in Acrobat Sign.
17. Under the Assign to People tab, in the People section check the box next to your name to assign at least one active user (yourself), then click Next.


18. Click Done.


You can now log out of Okta and proceed with testing your SAML setup. (See Testing Your Okta SAML SSO Configuration for more information.)
Setting Up Auto-provisioning in Okta
If this option is enabled, and the “Automatically add users authenticated through SAML” option in Acrobat Sign is also enabled, you can automatically provision users in Acrobat Sign.


Setting up Auto-launch for Acrobat Sign
You can automatically launch Acrobat Sign when you log in to Okta. If this feature is enabled, Acrobat Sign will open in a separate window when you log in to Okta. You must have pop-ups enabled in your browser for this feature to work.
Note If you also enabled the “Automatically log in when user lands on login page” option, when you launch Okta two Acrobat Sign windows will open.
1. Log in to Okta. Your Home page will display.
2. On the Acrobat Sign Provisioning app, cursor over the gear icon, then click to activate it.


3. When the Acrobat Sign Provisioning Settings popup displays, click the General tab.


4. Enable the Launch this app when I sign into Okta option.


5. Click Save.
Testing Your Okta SAML SSO Configuration
There are two ways to test your Okta SAML setup.
Log in to Acrobat Sign through Okta
1. If logged in, log out of Okta.
2. Log in to Okta. Your Okta Home page displays.
3. On the Home page, click the Acrobat Sign Provisioning app.


You are automatically logged into Acrobat Sign.


Log in to Acrobat Sign using your URL
1. Enter your company login URL in your browser. The Acrobat Sign Sign In page displays.
2. On the Sign In page, click the second Sign In button. If you’ve entered a custom Single Sign On Login Message that message displays above this button. If you have not entered a custom message, the default message displays.


You are logged into Acrobat Sign.


OneLogin Configuration
Overview
Acrobat Sign can support Security Assertion Markup Language (SAML) single sign-on (SSO) using external identity providers (IdPs) such as OneLogin. This document describes the steps for configuring Acrobat Sign for SAML SSO with OneLogin. This document also provides information on testing your SAML SSO configuration. Before proceeding, please see the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML setup process and provides detailed information on the SAML Settings in Acrobat Sign.
Configuring SAML SSO with OneLogin
1. Log in to OneLogin and Acrobat Sign in different browsers or in different windows within the same browser.
- In OneLogin, log in to your account with the same administrator credentials you use for your Acrobat Sign Admin Account.


- In Acrobat Sign, log in to your account using the same admin account credentials you use for OneLogin. The passwords for these two logins do not have to be the same, but you must log in as the administrator for each account.


2. In OneLogin, click Add Apps.


3. Search for Acrobat Sign.


4. Click the row for Acrobat Sign.


5. In the Add page, under Connectors select SAML 2.0 – user provisioning, then click Save at the top.


6. Navigate to the SAML Settings page. Note the Hostname for Acrobat Sign.


7. In OneLogin, click the Configuration tab. In the Subdomain field, enter your Hostname from Acrobat Sign, then click Save.


8. Click the SSO tab.


9. In the SSO tab, click View Details to display the Standard Strength Certificate (2048-bit) page.


10. In the Standard Strength Certificate page that displays, click the Copy to Clipboard button for the X.509 Certificate field to copy the certificate to the clipboard.


If the certificate successfully copies, the rollover text says “Copy to Clipboard” text updates to “Copied”.
11. In Acrobat Sign, paste the copied certificate into the IdP Certificate field. Be sure to remove any returns that may have been copied. The cursor should be at the end of the last line as shown below.


12. In OneLogin, click the Copy to Clipboard button for the Issuer URL.


13. In Acrobat Sign, paste the Issuer URL into the Entity ID/Issuer URL field.


14. In OneLogin, click the Copy to Clipboard button for the SAML 2.0 Endpoint (HTTP) URL.


15. In Acrobat Sign, right click to paste the SAML 2.0 Endpoint (HTTP) URL in the IdP Login URL field.


16. In OneLogin, click the Copy to Clipboard button next to SLO Endpoint (HTTP).


Note: The OneLogin SAML 2.0 Endpoint URL is only a suggestion. You can actually specify any valid URL (e.g., Google).
17. In Acrobat Sign, copy the SLO Endpoint value into the Logout URL/SLO Endpoint field.


18. In Acrobat Sign, click Save.
19. In OneLogin, click the back arrow to return to the SSO page.


20. Click the Users tab to add users.


21. Click the row to add the user. The Save button is not activated until you click at least one user.


22. When done, click Save.
Testing Your OneLogin SAML SSO Configuration
There are two ways to test your OneLogin SAML Setup.
Log in to Acrobat Sign through OneLogin
1. If logged in, log out of Acrobat Sign.
2. Log in to OneLogin.


3. On the App Home page, click the Acrobat Sign app.


You are automatically logged into Acrobat Sign.


Log in to Acrobat Sign using your URL
1. Enter your company login URL for Acrobat Sign in the address line of your browser (such as myCompany.adobesign.com). The Acrobat Sign Sign In page
displays.
2. On the Sign In page, click the second Sign In button. If you’ve entered a custom Single Sign On Login Message that message displays above this button. If you have not entered a custom message, the default message displays.


3. You are logged into Acrobat Sign.


Oracle Identity Federation Configuration
Overview
Acrobat Sign can support Security Assertion Markup Language (SAML) single sign-on (SSO) using external identity providers (IdPs) such as Oracle Identity Federation (11g). This document describes the steps for configuring Acrobat Sign, acting as the SAML consumer or service provider (SP), to use OIF. This document also provides suggested steps for configuring OIF, however, please contact your OIF system administrator before making any configuration changes to your OIF Server. Before proceeding, please see the Acrobat Sign Single Sign On Using SAML Guide, which describes the SAML set up process and provides detailed information on the SAML Settings in Acrobat Sign.
Configuring OIF as an IdP in Acrobat Sign
Your organization’s instance of OIF needs to be configured within Acrobat Sign as the external SAML Identity Provider (IdP). As an administrator for your Acrobat Sign Account, navigate to SAML Setting in Acrobat Sign as an (Account | Account Settings | SAML Settings).
You will need metadata information from your OIF IdP
configuration. Typically, the metadata for the OIF is available as an XML
content at: http://:/fed/idp/metadata.
Please contact your OIF administrator to gather the relevant. You will need the
following configuration information.
- Entity ID/Issuer URL—The entityID attribute on EntityDescriptor element
- Logout URL/SLO Endpoint—When someone logs out of Acrobat Sign, this URL is called to log them out of the IdP as well.
- Login URL/SSO Endpoint—The Location attribute on SingleSignOnService element
- IdP Certificate—Certificate information under the element EntityDescriptor -> IDPSSODescriptor -> KeyDescriptor use="signing"
This information should be configured in the appropriate fields in the Acrobat Sign SAML configuration. See the image below:

Configuring Acrobat Sign as a SP in OIF
Once the OIF SAML configuration is complete within the Acrobat Sign UI, the next step is to configure Acrobat Sign as a Service Provider within OIF. The information required for configuring Acrobat Sign within OIF is available on the Acrobat Sign SAML Service Provider (SP) information section under Account | Account Settings | SAML Settings.


The metadata description for Acrobat Sign is shown below:


You must customize this metadata description and change the highlighted section in the XML to match the URL for your account. The Assertion Consumer URL for your specific account is shown in SAML Settings.
The steps for completing the configuration in OIF are as follows:
1. Go to the Federations configuration screen on the OIF Administration panel


2. Create a new federation profile


3. Create a new Service Provider (SP) listing for Acrobat Sign.
Import the Acrobat Sign SP configuration XML or manually create the SP listing using the provider information from the Acrobat Sign SAML settings.


4. Complete the configuration. Acrobat Sign will appear as a new Service Provider listing in the OIF list of SPs.


Verifying Email Address as NameID Format
Acrobat Sign uses email addresses as the unique user identifier. Before testing the single sign-on one last step is the ensure that the email address field is mapped to the appropriate user attribute within OIF and that the email address is enabled as a valid NameID format.




Known Issues
Redhat IdP has a setting called Encrypt Assertions that adds an additional layer of encryption.
This additional encryption is incompatible with the Acrobat Sign SAML configuration, and should not be enabled for Acrobat Sign.


©2022 Adobe Systems Incorporated. All Rights Reserved.
Products mentioned in this document, such as the services of identity providers Microsoft Active Directory Federation, Okta, Onelogin, and Oracle Identity Federation, and Salesforce software retain all of the copyrights and trademark rights of their specific corporations.